DO YOU HAVE
A STRATEGY TO PROTECT
YOUR BUSINESS?
DO YOU HAVE
A STRATEGY TO PROTECT
YOUR BUSINESS?

SOCI Act Compliance
The Australian Cyber Security Strategy 2020 will invest $1.67 billion over 10 years to achieve our vision of creating a more secure

Managed Security
Cybersecurity assessments and implementations are essential for businesses of all sizes. They help to identify

Essential 8
The Australian Cyber Security Centre (ACSC) recommends eight essential strategies to prevent malware delivery, limit
Welcome to Cyber Ethos
The cybersecurity landscape is changing everyday to tackle the dynamic threats. These threats can range from a ransomware/crypto-locker to a phishing/brute-force and denial-of-service attacks. Be proactive and build a resilient cybersecurity response to protect your business and its most critical processes from the impact of cyberattack.
Protect your business and assets
Cybersecurity breaches result in financial loss, damage to business image as well as jeopardise future business. Cyber Ethos will help you strengthen your defenses and protect your business against cyber threats.
Protect your business and assets
Cybersecurity breaches result in financial loss, damage to business image as well as jeopardise future business. Cyber Ethos will help you strengthen your defenses and protect your business against cyber threats.
Comprehensive Cyber Security Services
Cybersecurity
Strategy
A cybersecurity strategy is essential for any business, regardless of size or industry. It provides a roadmap for protecting
Consulting and
Advisory
In today’s digital landscape, effective cybersecurity is more than just a technology solution – it’s a strategic imperative.
Critical Infrastructure
(ICS/SCADA)
As the threats of cyberwarfare and cyber-terrorism loom over the world, the security of critical infrastructure is a national priority
CISO as a Service
A Chief Information Security Officer (CISO) is a senior executive responsible for overseeing an organisation’s cybersecurity
Cybersecurity at the Board
Cybersecurity is a top priority for businesses of all sizes. Cyberattacks can have a devastating impact on a business
Forensics and Incident Response
Time is of critical essence when it comes to successfully countering and containing a cyberattack! Welcome to Cyber Ethos

How a cybersecurity breach can affect your business
A cybersecurity breach can have significant and far-reaching consequences for a business, impacting various aspects of its operations, reputation, legal standing and finances. Preventing breaches through robust cybersecurity measures is essential to mitigate these risks and protect the organization’s overall well-being. Without a sound cybersecurity strategy, a business can be severely affected in various aspects:
- Financial Loss
- Operational Disruption
- Legal and Regulatory Consequences
- Reputational Damage
- Increased Security Costs
- Customer and Employee Impact

- Financial Loss
- Operational Disruption
- Legal and Regulatory Consequences
- Reputational Damage
- Increased Security Costs
- Customer and Employee Impact
CYBERSECURITY FAQ’S
Cybersecurity involves protecting your digital systems, networks, and data from theft, damage, or unauthorized access. It’s vital for your business to safeguard sensitive information, maintain customer trust, and ensure uninterrupted operations.
Common threats include malware, phishing, ransomware, insider threats, and DDoS attacks. Cybercriminals exploit vulnerabilities in your systems to compromise data or disrupt operations.
Conduct a risk assessment by identifying potential threats, vulnerabilities, and the impact of a breach. This helps prioritize security measures.
Conduct a risk assessment by identifying potential threats, vulnerabilities, and the impact of a breach. This helps prioritize security measures.
Employee training is crucial in preventing social engineering attacks like phishing. It educates staff on recognizing and responding to threats appropriately.
Implement encryption, access controls, and data backups. Regularly update software and use strong passwords. Also, classify data according to its sensitivity.
2FA requires users to provide two separate forms of identification before granting access. It adds an extra layer of security, making it more difficult for unauthorized individuals to access accounts.
Regularly back up data, keep software updated, use robust antivirus software, and educate employees on ransomware threats. Be cautious about opening email attachments and links.
GOT QUESTIONS?
WHAT OUR CLIENTS SAY
OUR EXPERIENCE
We bring the real-life experience, skills, and knowledge you need, from having led technology teams, projects, business functions, and complex cybersecurity transformations & cybersecurity awareness training across multiple government departments, critical infrastructure, not for profits and privately owned organisations.



















Use of AI and Blockchain in cybersecurity
Blockchain and AI (artificial intelligence) are two potent technologies that are rapidly being used in cybersecurity…
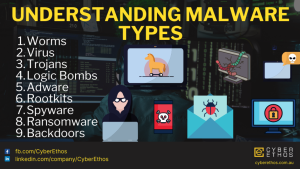
Different Types of Malware
Malware, a contraction of “malicious software,” is any program created with the express purpose of…

What is cybersecurity forensics?
Cybersecurity forensics involves gathering, conserving, analyzing, and presenting electronic…
CISA Updates
All Products
Source: All Products Published on 2023-11-02
Source: All Products Published on 2023-11-02
Source: All Products Published on 2023-11-02
Source: All Products Published on 2023-11-02
Cybersecurity Advisories
Source: CISA Current Activity Published on 2023-11-02
Source: CISA Current Activity Published on 2023-11-01
