Articles

Use of AI and Blockchain in cybersecurity
Blockchain and AI (artificial intelligence) are two potent technologies that are rapidly being used in cybersecurity…
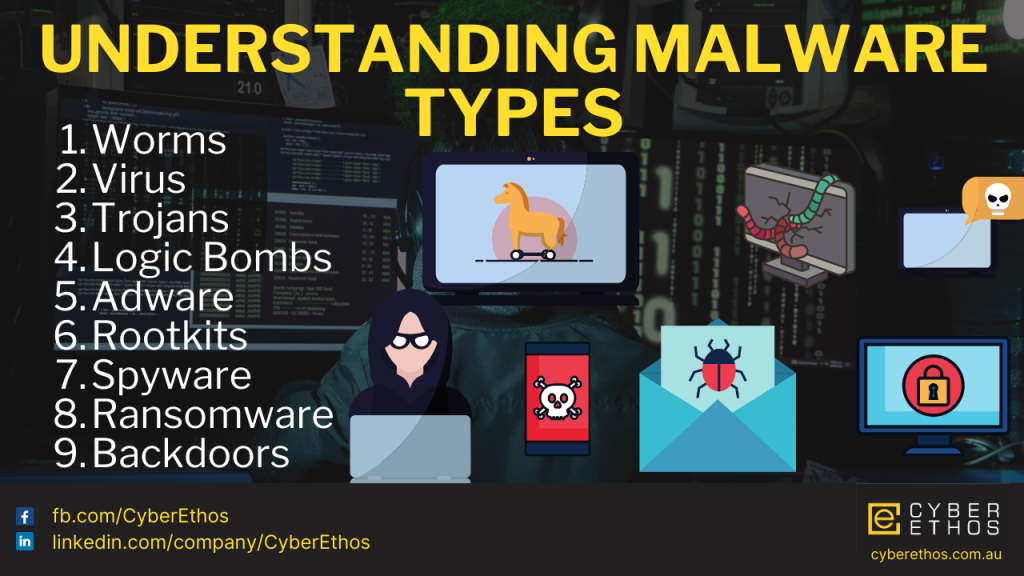
Different Types of Malware
Malware, a contraction of “malicious software,” is any program created with the express purpose of…

What is cybersecurity forensics?
Cybersecurity forensics involves gathering, conserving, analyzing, and presenting electronic…

What are the key cybersecurity best practices for remote work and the hybrid workplace model?
As remote work and hybrid workplace models become more prevalent, ensuring the security of your organization’s data

How can we protect our organization from ransomware attacks, which have been on the rise recently?
Protecting your organization from ransomware attacks, which have indeed been on the rise, requires a multi-faceted

What are the most significant cybersecurity threats for organizations in 2023?
Cybersecurity threats continue to evolve, and in 2023, organizations will face a variety of significant threats. Some of the most

Top 5 Safeguards Against Zero-Day Attacks
Cybersecurity threats continue to evolve, and in 2023, organizations will face a variety of significant threats. Some of the most

Critical Security Update Alert - Chrome Browser
Google has just released crucial security updates to address multiple vulnerabilities in the Chrome browser, spanning across

What are Network forensic tools in cybersecurity forensic?
Network forensic tools play a critical role in cybersecurity because professionals use them to investigate and analyze network

What are Malware analysis tools in forensic?
Malware analysis is a crucial element of cybersecurity forensics that involves evaluating malicious software …

What are Memory analysis tools in forensic?
In forensic cybersecurity investigations, memory analysis is an important step where investigators inspect a computer…

Understanding APRA Prudential Standard CPS 234 Information Security: A Comprehensive Guide
The Australian Prudential Regulation Authority (APRA) is the regulatory body in….
